Introduction
The Weekly Report collects metrics for every network, service, and device monitored by Field Effect during a week and tracks weekly trends over time.
Use these reports to detect early signs of vulnerabilities. As they are generated over time, you'll gain historical context that can help gauge the progress of your organization’s security posture. Reports can be viewed or downloaded from the Reports View.
Table of contents
Sample Weekly Report
The following image shows the Weekly Image in its entirety.
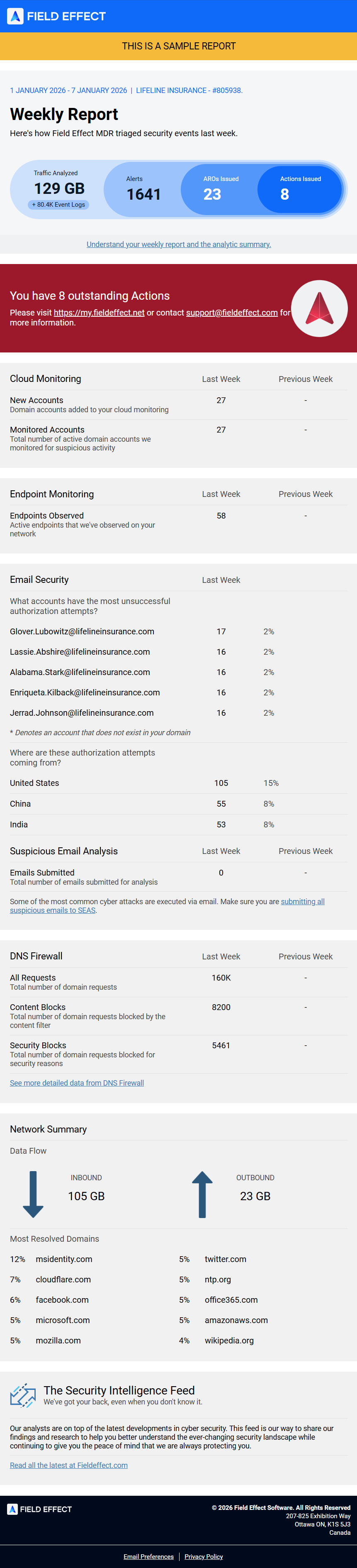
The Sections of the Weekly Report
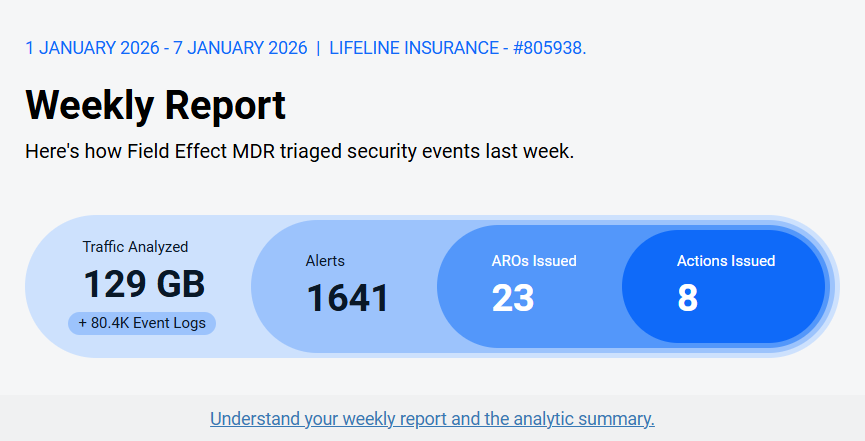
Overall Status
At the top of the report, you can get a snapshot of your overall security posture. Any outstanding Action AROs will be highlighted as a reminder to follow up and resolve the issue(s).
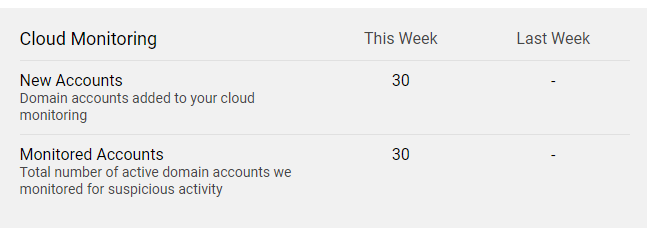
Cloud Monitoring
Here you can see statistics on your cloud services, such as the number of newly created accounts for the week, and the number of total users being monitored for suspicious activity.
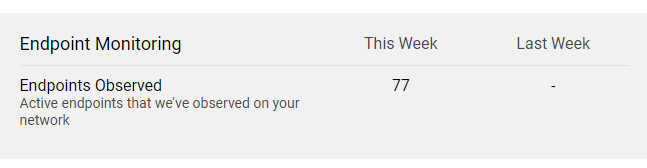
Endpoint Monitoring
This section shows the number of new, as well as active, endpoints Field Effect discovered on your network.
Email Security
This section summarizes the most targeted email accounts in terms of unsuccessful authorization attempts and their locations. The percentage attributed to each email account represents their total percentage of all authorization attempts.
In the example below, the account "Zachariah.O'Connell@balticauto.com" had 19 unsuccessful authorization attempts, representing 3% of all attempts. And of these attempts, the top three locations they are coming from are the United States. India, and China; with the United States at the top spot, with 101 attempts representing 15% of all attempts.
If your organization has SEAS enabled and actively submit emails to the service, high-level details including the number of emails submitted week over week, and the number of emails which were deemed suspicious or malicious, are shown in this section.

DNS Firewall
The DNS Firewall section presents details about requests and blocks with a week over week comparison. You can also follow the "See more detailed data from the DNS Firewall" link to access more granular details on the Field Effect MDR Portal.

Network Summary
From the Network Summary section, you can view the amount of inbound and outbound traffic to occur with the week, as well as the domains that saw the most resolution, and the total percentage each domain represents.

The Security Intelligence Feed
To enrich the report with news and general cyber security topics, the report includes a link to our Security Intelligence Feed. Here you will find our thoughts, analyses, and best practices surrounding the latest news and events in cyber security.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article