Introduction
Whenever Field Effect MDR discovers a piece of "vulnerable" software (out of date, end of life), it is reported in your monthly ARO for vulnerable software. While the monthly ARO for vulnerable software includes a list of endpoints that were affected at the time the ARO was generated, this table lists all devices that are currently affected by vulnerable software.
This table is refreshed every hour.
Suppressing Vulnerable Software AROs
If you prefer to work exclusively with supplemental data tables to deal with software management, and not receive any AROs for vulnerable software, you can choose to have vulnerable software AROs suppressed entirely. The monthly AROs sent for vulnerable software will no longer be generated, but this table will always report the most recent (within an hour) list of devices with vulnerable software installed.
To learn more about ARO suppression, see:
See the Supplemental Data Page - Overview for more on how AROs can be suppressed.
Viewing the Vulnerable Software Table
This table lists all devices, and all software, that are currently vulnerable. There are several columns reporting on the details of each device, much like the MDR Portal's Devices page.
Columns to focus on when addressing vulnerable software include:
- Name: the name of the vulnerable software.
- Version: The version of the software currently installed.
- Install Path: the location where the software is installed on the endpoint device.
- Severity: the severity level communicated the level the urgency that should be placed on the vulnerability.
- Hostname: the name of the endpoint device.

Filtering the Table
You can narrow the results of this table using the three search bars (hostname, software name, and CVE ID) and two filters (operating system and severity) available at the top of the page. Typing into a search bar will begin to narrow the results against the appropriate column and your search parameters. The dropdown filters can be used independently or with a typed search.
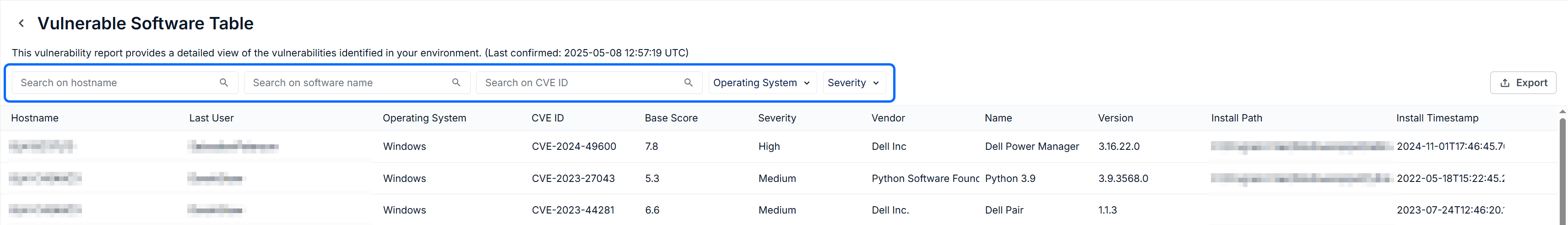
Exporting the Table
If you would like to take this list with you as you address the impacted devices, click the Export button to download the current list a .csv file.

Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article