Introduction
Antivirus Management, powered by our endpoint agent, allows endpoint devices (with the agent installed) to report back to the appliance about the status and configuration of the device's Antivirus:
When enabled, Antivirus Management can report the following back to the MDR Portal:
- Whether or not an antivirus is installed on the device.
- Which antivirus is installed on the device.
- Micrsoft Defender Antivirus only:
- See details about how Defender is configured on the device (audit mode).
- Set a Defender configuration that the endpoint agent will enforce across all devices (enforce mode).
- This is currently only available for Defender Antivirus, the component built into Windows. This is not supported for the cloud-based, enterprise level version, Defender for Endpoint.
While enabling the feature, you have the opportunity to define which Defender settings and configurations are considered "compliant" or "non-compliant" to your organization. As endpoint agents update with the appliance every few minutes, any "non-compliant" configurations will be reported on the MDR Portal's Devices page. If enforce mode is enabled, the endpoint agent will change the Defender Antivirus settings to your organization's preferred configuration, which are set in the MDR portal.
Supported Microsoft Defender and Windows Versions
Field Effect MDR's advanced Managed Antivirus features (audit and enforce) are currently only available for Defender Antivirus; the component built into Windows. This is not supported for the cloud-based, enterprise level version, Defender for Endpoint.
Microsoft Defender Antivirus is built into and enabled by default for Windows 10 and 11, as well as Windows Server 2016 and later. If your organization has a paid subscription for Microsoft Defender for Endpoint (cloud version), Microsoft will support Defender Antivirus for a wider range of Windows versions, including older ones like Windows 7 SP1 and Windows Server 2008 R2. Versions that have reached end-of-life may also require you to be a part of an ‘Extended Security Updates’ (ESU) paid program.
Currently, Field Effect MDR's Managed Antivirus advanced features are only supported for Microsoft Defender on Windows 10 and 11, Enterprise versions of Windows 8.1, and Windows Server 2016 (or newer) - even if your organization has one of the aforementioned subscriptions or ESUs in place.
Enabling the Feature
For more details on enabling the feature, and all of the preference options available, see Enabling Antivirus Management.
When setting up the feature, it can be enabled to use one of two distinct modes:
- Audit: when selected, the endpoint agent will only report on the device's Microsoft Defender settings; changes will not be made to devices that do not comply with your chosen configurations.
- Enforce: when selected, the endpoint agent will change Microsoft Defender settings that do not comply with your chosen configurations.
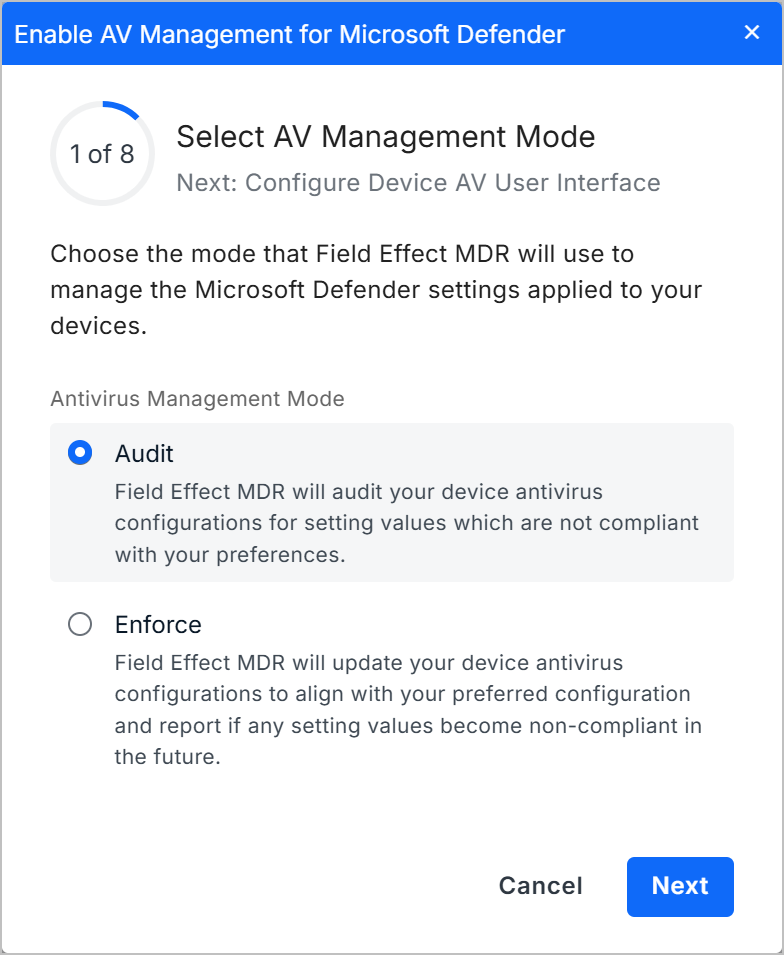
As you continue through continue through the wizard, you will set your preferred Defender settings which will be reported on (audit mode) or changed to the compliant setting (enforce mode).

Antivirus Management: Reporting
After you enable the feature, the Antivirus Management reporting is
Once enabled, the Devices page will start to show Antivirus Management reporting. The following Devices Page columns are available for this feature:
- Detected Antivirus: the name of the antivirus currently present on the endpoint device.
- AV State: the current state of the present antivirus.
- AV Compliance: reports on whether the endpoint’s Defender settings are compliant with your preferred settings, as dictated on the MDR Portals Administration>Antivirus Management page.
- AV Last Scan: The last time Microsoft Defender scanned the endpoint device for threats.
- AV Last Signature update: The last time Microsoft Defender updated its signatures on the device.
These columns may not be visible be default. To enable them, click Columns dropdown menu and enable your desired columns. To learn more about filtering and sorting this view, see Sorting, Search, and Filtering the Endpoint Devices Page.

Drilling into a Device for Antivirus Metrics
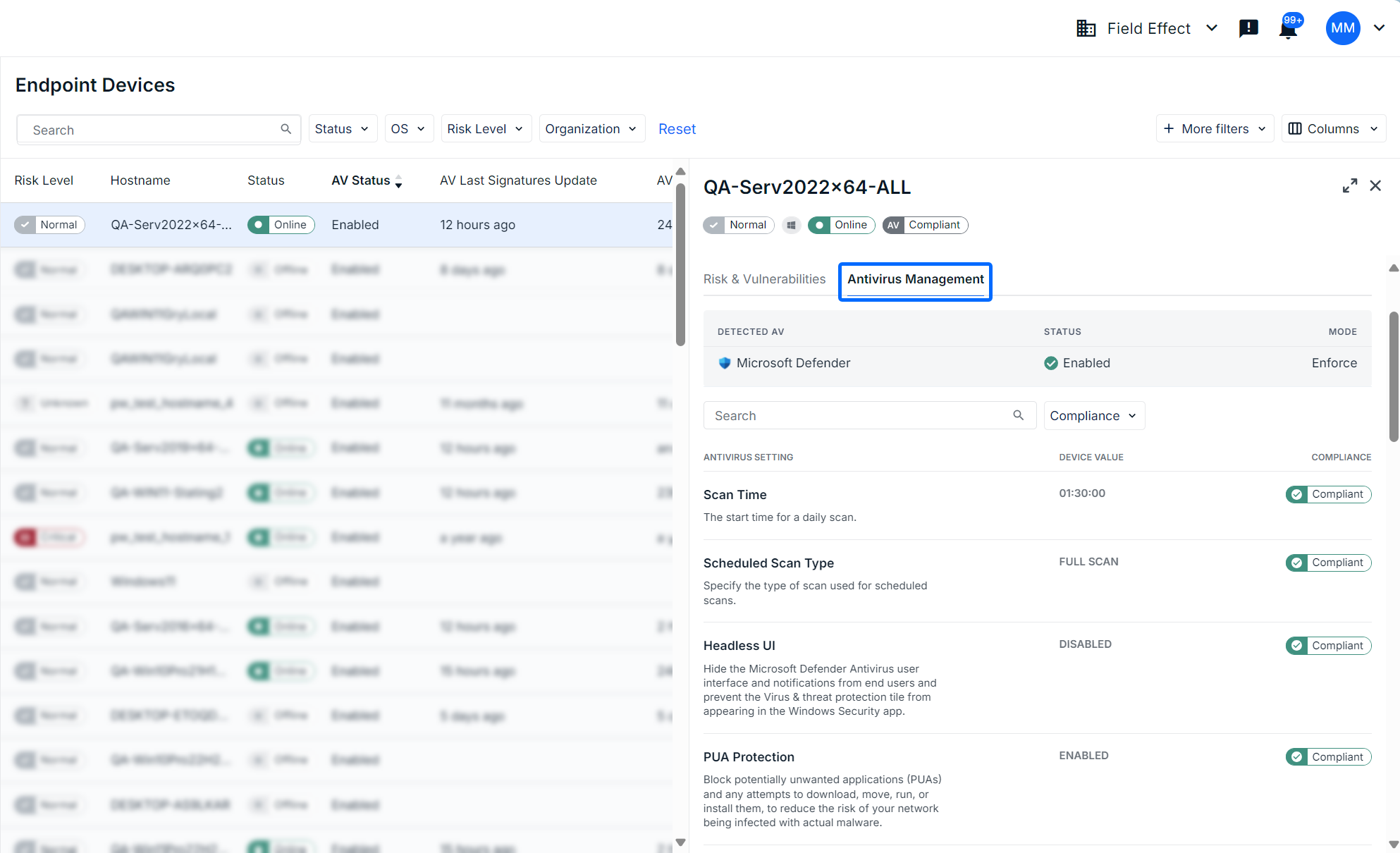
When drilling into a device on the Endpoint Devices page’s main table, you can see more granular details about the device’s antivirus configuration and whether or not it’s compliant. To drill into a device, click on the host name of the device on the main table (shown above).

The drilled in view will open on the right side of the table showing all of the device's details. Click the Antivirus Management tab to see details about that device's Microsoft Defender configurations. You can scroll through, as well as search, the endpoint device's Microsoft Defender configurations.
In the example below, the endpoint device has Microsoft Defender enabled, and its configurations are compliant.
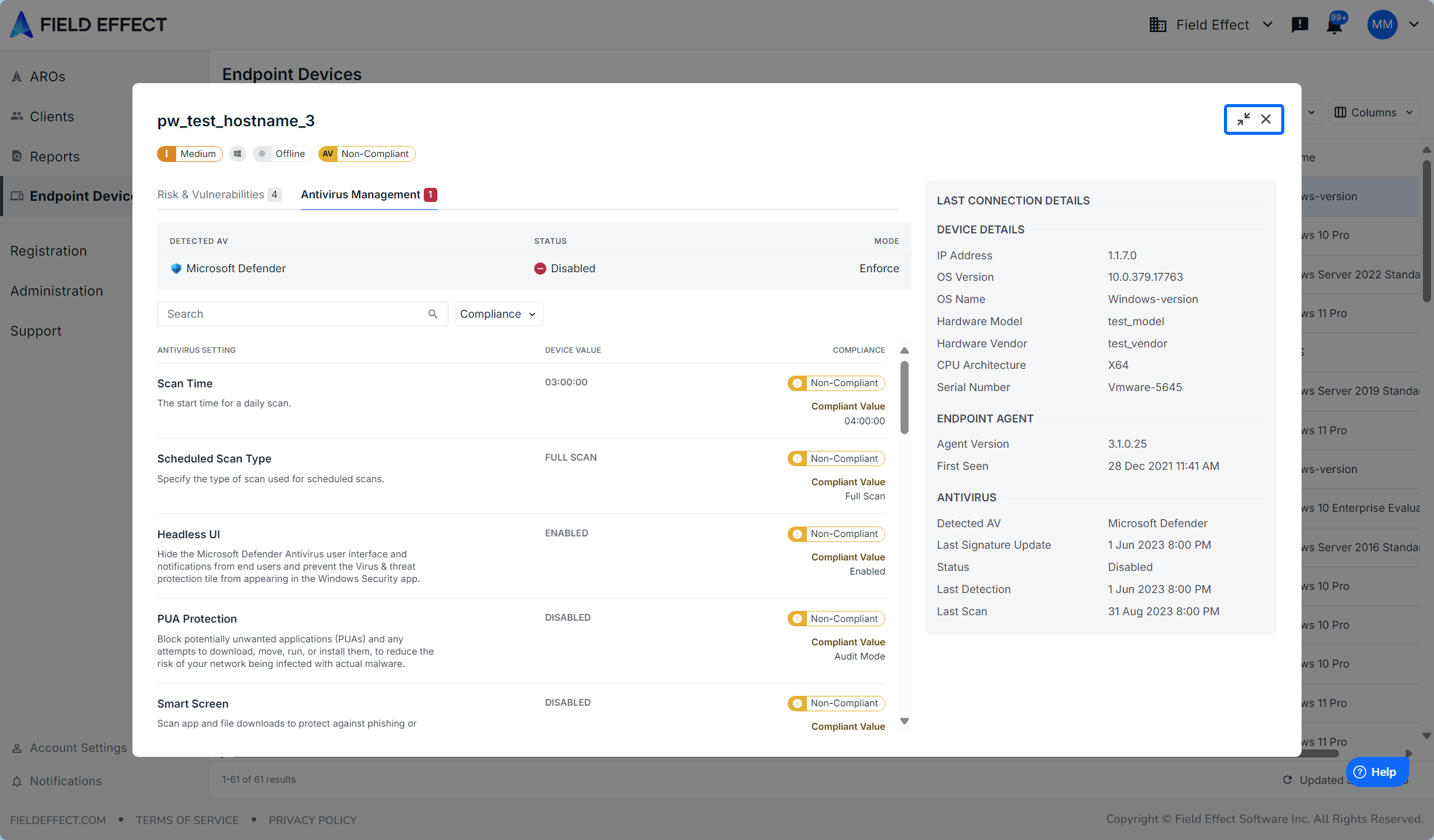
Clicking the expand icon will open the drilled inside view as a new window. In the example below, Microsoft Defender has been disabled on the endpoint device, therefore all of the configurations are not compliant. Since the organization is using enforce mode, the next time the device is online, the endpoint agent will re-enable Defender and set configurations to your organization's preferred states.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article