Introduction
A summary of the physical network appliances and their specifications. This article will also summarise Primary Vs Secondary appliances, an overview of the cabling for port-mirrored & inline configurations, analytics and conclude with physical appliance specifications.
Table of contents
- Overview of Physical Appliances
- Primary Vs Secondary Appliances
- Deploying Appliances
- Appliance Analytics
- Physical Appliance Specifications
Overview of Physical Appliances
Our physical network appliances are installed within your infrastructure to power Field Effect MDR's network monitoring capabilities. Available in several form factors to accommodate different network and storage requirements, appliances can be used as either a primary or secondary appliance and deployed in either a port mirrored or inline configuration.
Once deployed in the network, it captures, stores, and analyzes all packet traffic leaving or entering. Endpoint device telemetry is also relayed to the appropriate appliance, via endpoint agent, for analysis.
As the primary appliance receives data from the network, endpoint devices, and any other secondary sensors sending telemetry, the sensor technology on the primary appliance analyzes it. Field Effect MDR will then either act to stop a threat (example: Active Response) or report on a risk via ARO, report, or dashboard.
This article outlines the two appliance types (primary and secondary), the form factors available for them, how they can be deployed (port mirrored or inline), and the analytic capabilities within the appliance’s sensor technology.
Primary Vs Secondary Appliances
Primary appliances have our sensor technology installed, which analyzes all of your organization’s data and telemetry. If your organization has a single Field Effect appliance, it is the primary appliance collecting and analyzing all data.
If your organization has several appliances deployed across several locations and networks, one appliance (usually deployed at the headquarters) will be assigned as the primary appliance. Secondary appliances may be installed in other network or branch locations and do not analyze data – they only relay collected data to the primary appliance for analysis.
Deploying Appliances
The following section outlines the different connections used for our appliances and the available deployment configurations.
Appliance Connections
There are several color-coded connection ports on each appliance, and they are used for the following:
| Color | Port-Mirrored | Inline | Connection Notes |
|---|---|---|---|
| Green | Required | Required | Connects the appliance to an internal switch. Managed connection for backup and managed service connectivity. Accepts a DHCP lease from the LAN (DHCP reservation is recommended). |
| Yellow | Required | Required | Port mirrored: connects the appliance to a SPAN sport Inline: inbound connection from the WAN to the appliance. |
| Blue | No | Required | Connects the appliance to the LAN port (core network switch). |
| Red | Optional | Optional | Alternative management connection when a static IP is required. The IP address, subnet, default gateway, and DNS will need to be configured using the appliance management console. |
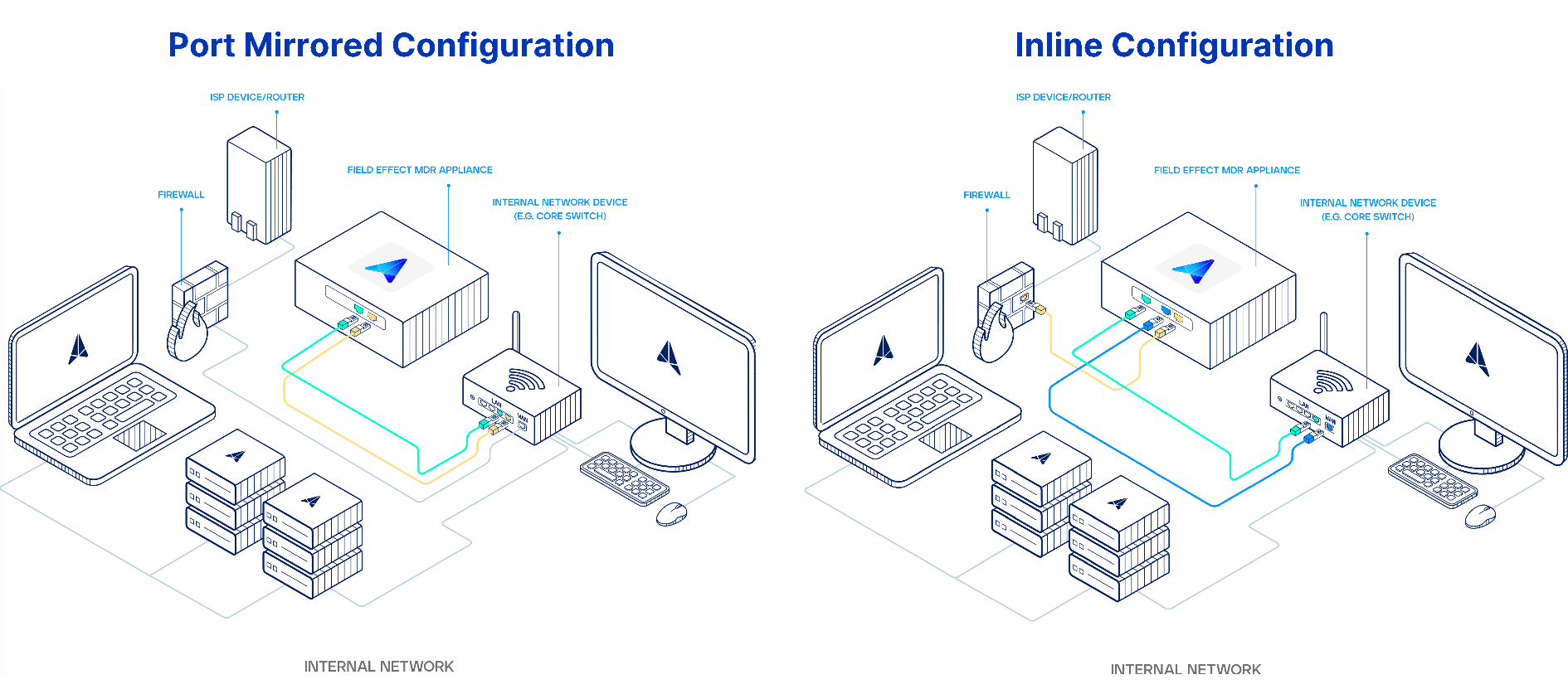
Deployment Configurations (Port Mirrored or Inline)
Traffic monitoring via the MDR appliance is passive. During normal operations, the appliance will not interfere with traffic. If the appliance is reset or powered off, the network card has a feature that bypasses the ports, maintaining the network connection.
Our appliances can be deployed in either a port mirrored or an inline configuration. For more on deploying our appliance, visit our knowledge base for general deployment guides, or guides specific to your appliance.
- Port Mirrored Configuration:
- In a port-mirrored configuration, the appliance is connected out-of-band to a single LAN interface. Your network equipment (firewall or switch) must be configured to enable port mirroring (also called spanning port), to copy and send traffic from tagged ports to a single destination port. .
- Inline Configuration:
- The appliance sits in between your network's primary switch and firewall. All network traffic is directly passed from the switch, through the appliance, and then out to the firewall.
Appliance Analytics
Primary appliances perform high-resolution deep packet inspection and protocol analysis on all IPv4 and IPv6 network traffic that passes through, or is mirrored to, the primary appliance. For additional analysis, Field Effect can collect syslog or NetFlow data from the network and retains raw data as packet captures (PCAPs) where possible.
Field Effect extracts information from network traffic that supports security monitoring. This includes passively identifying network services and fingerprinting devices, collecting DNS resolutions, monitoring connections, and identifying scans. The network sensor technology evaluates network signatures to alert on known malicious activity.
The appliance performs the following operations:
| Operation | Description |
|---|---|
| Full Packet Network Capture | Captures, analyzes, and stores (in PCAP format) full network traffic for IPv4 and IPv6 networks. |
| Network Edge Monitoring | Monitors for threats and vulnerabilities across all devices within a network. |
| Endpoint Sensor Management | Manages endpoint agents, which includes collecting, storing, and analyzing all telemetry. |
| Log Ingestion Capabilities | Ingests salient log data from external sources, enriching security context. Log data may be ingested from anything that can generate ‘syslog’ formatted data. Field Effect also supports RFC3164 and Common Event Format (CEF) messages. |
Network Analytic Categories
The following section outlines the threat surface and threat detection categories used by the appliance’s on-device sensor technology that are relevant to network monitoring.
| Category | Sub-Category | Description and Examples |
|---|---|---|
| Network Risk | Insecure Configurations | Use of legacy protocols, legacy encryption, or weak cipher suites. |
| Exposed Services | Public IP addresses accessing services such as Remote Desktop Protocols (RDP), Secure Shell (SSH), File-Transfer Protocol (FTP), Server Message Block (SMB). | |
| Asset Identification | legacy devices and new Internet-of-Things (IoT) devices. | |
| Threat Detection | Data Loss | Abnormal patterns of data transfers (endpoint, network and cloud-based). |
| Lateral Movement | Endpoint and Network-based detections. | |
| Internal Network Scans | Connection patterns indicative of a device performing port scanning across the network. | |
| Connections | Any connections associated with known-bad indicators of compromise. | |
| Discovery | Internal network scanning. | |
| Suspicious Connections | Node behavior deviation and fixed interval communication (beacons) that may be indicative of malware. |
Physical Appliance Specifications
If you would like to see images of each appliance, please visit the configuration guide for your appliance.
| Specification | Compact One | Oskar (Legacy) | Business One | Enterprise One | Enterprise One Hundred | |
|---|---|---|---|---|---|---|
| Dimensions | Width | 133mm (5.24") | 200.66mm (7.9") | 246mm (9.5") | 434.00mm (17.08") | 434.00mm (17.08") |
| Depth | 98mm (3.86") | 248.92mm (9.8") | 270mm (10.5") | 595.63mm (23.45") | 737.50mm (29.00") | |
| Height | 35mm (1.38") | 71.12mm (2.8") | 107mm (4.2") | 1RU | 2RU | |
| Rack Unit Size | NA | NA | NA | 1RU | 2RU | |
| Weight | < 1 lbs.bs | 3.43Kg (7.56lbs) | 5.8Kg (12.79lbs) | 13.6Kg (29.98lbs) | 33.1Kg (73.0lbs) | |
| Power Supply Unit | 48W (with twisat lock) | 180W | 180W (with locking plug) | Dual 350W | Dual 1100W | |
* Appliances are managed remotely by Field Effect.
** These ports are listed for information only and aren’t relevant for the management of the appliance or Field Effect.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article