Introduction
Partners: This page, and the Insights section as a whole, are only available when the organization selector is set to a specific client view.
The My Network page includes the following sections:
- Status and Time Range: shows the network connection and contains a date range tool for the page.
- Summary: a graph for inbound and outbound traffic monitored over a given time range.
- Security Events: a spider chart organizing security events by type and frequency.
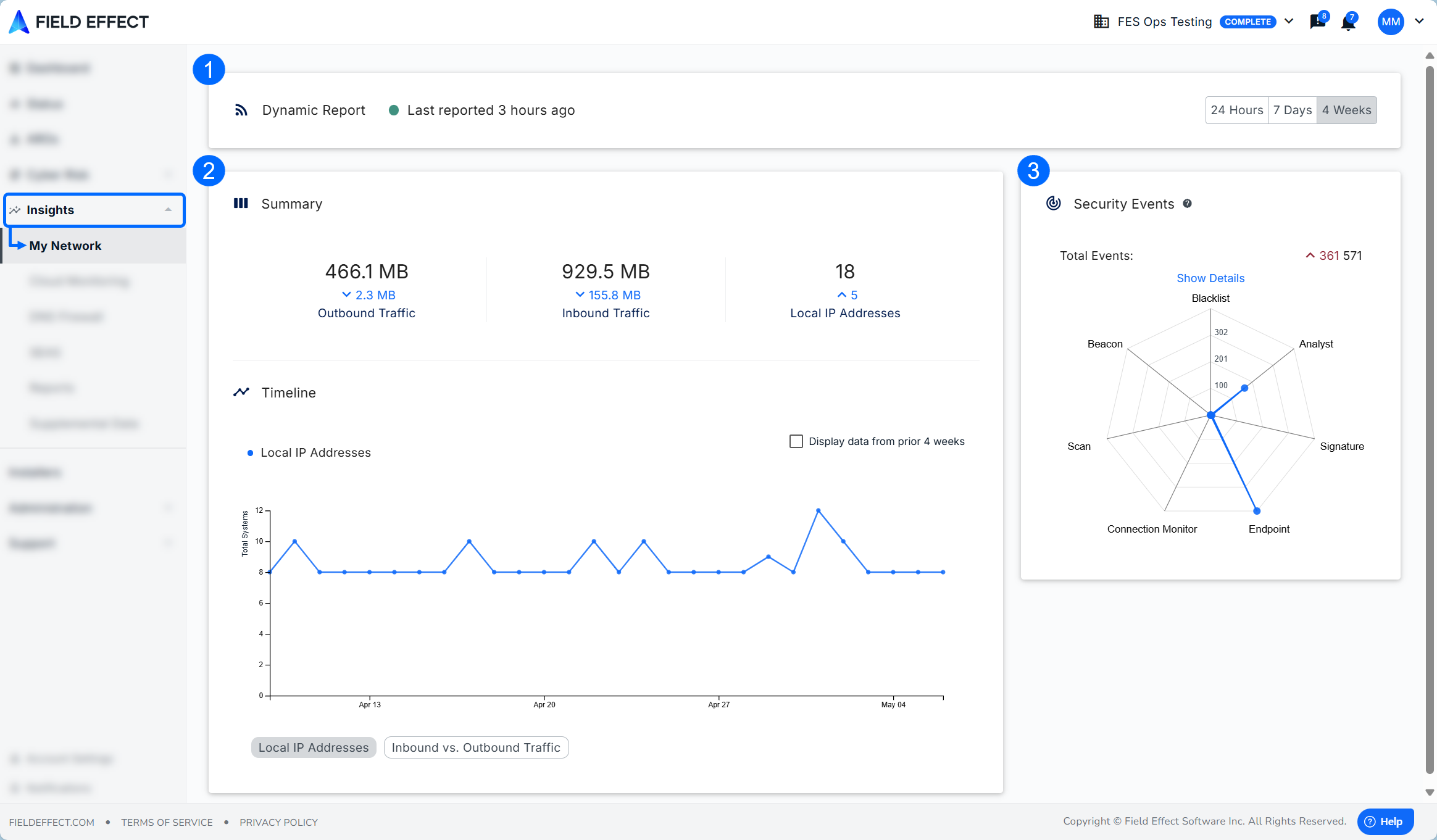
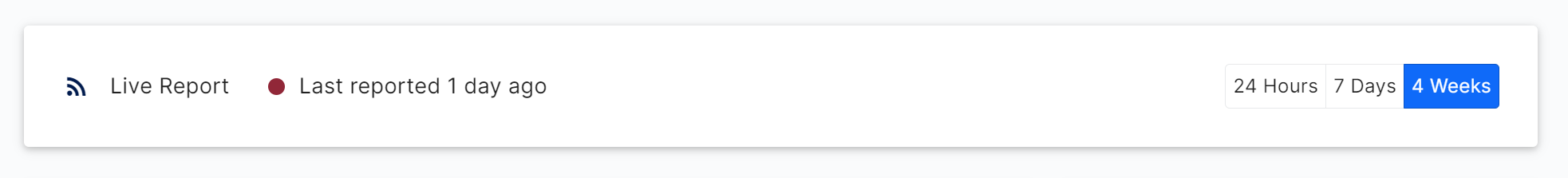
Status & Time Range
This section at the top of the page shows a network status indicator and the time range tool for switching the page to show data for a 24-hour, 7 days, or 1 month range.
Summary
This graph aggregates the total inbound and outbound traffic for your network and IPs. Details for each metric are graphed out in the timeline. You can include last month’s data in the upper right and change the graph’s metrics to one of the following:
- Inbound vs Outbound traffic
- Local IP Address traffic

Security Events
Security events that take place (within the selected range) are displayed in a spider chart. The further from the center a datapoint is, the more those events occurred within the selected time range. In the example below, analyst and endpoints events occurred the most within the selected range.
Click Show/Hide Details to see more about each item on the chart.
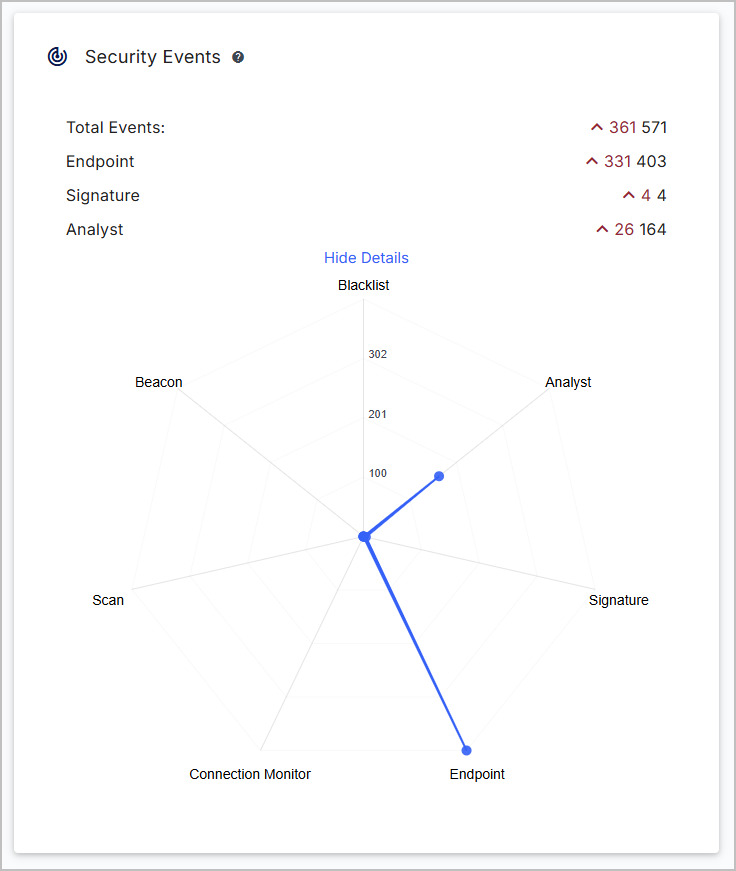
Security Event Types
The following sections provide definitions of each security event available in the graph.
Blacklist
These events are based on dynamic lists of indicators, usually domain names and IP addresses, which are produced and shared by security researchers and professionals. False positive events in blacklist monitoring are extremely common which is why these events alone are rarely a sufficient indication of an issue. Instead, these events are combined with, and used to augment other analytics.
Beacons
Beacons are periodic communications from your network to systems on the Internet. Beacons are commonly used by software to manage updates and maintain connections. Unfortunately, malware and other types of unwanted attack activity often use beacons as a method of command and control, and data exfiltration.
Scans
Scanners are automated tools that seek to identify systems on the Internet and gather information about them. Most scanning activity is benign; however, it is also a common precursor to an attack. Field Effect leverages advanced analytic profiling techniques to identify and alert on suspicious scans that could indicate a potential threat as well as those of Internet researchers and security firms.
Endpoint
These events are derived from the endpoint agent and includes events that trigger an ARO directly, as well as events like suspicious processes and other system events that may require some investigation. So, it’s not uncommon to see a count of events here higher than the number of endpoint-derived AROs you received, that just means the team has assessed some events as benign.
Signature
These are events are primarily network-based signatures which are a form of IOC and the supplemental detection mechanism within Field Effect. Signatures can be of high confidence and immediately trigger an ARO, but they can also produce false-positive events - which are vetted by our team and will not result in an ARO. So, you may see signature events that don’t have an associated ARO.
Analyst
Analyst events are the broadest and capture events produced by our evolving set of analytics. Some analyst events may not generate an ARO, so they are frequently rolled up into a group or summary ARO that is related to simple issues like patching, service configuration, and so forth. This category also includes new analytics that are being developed, supplemental events used to validate/confirm other analytics, and many other event types that do not produce an AROs immediately. So, it is also common to see more Analyst Security Events than related AROs.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article