Introduction
This article describes the Field Effect MDR integration with Amazon Web Services (AWS). This article covers the following:
Integration Details
This integration allows Field Effect MDR to monitor AWS with a focus on audit logging data. We monitor AWS's management plane (via CloudTrail) to monitor "who did what, and when" within you AWS environment (Learn more).
If AWS GuardDuty is enabled in your environment, Field Effect will be able to monitor these findings. GuardDuty generates a finding whenever it detects unexpected and potentially malicious activity in your AWS environment. (Learn more).
We currently do not monitor the CloudTrail data plane.
Requirements
To complete this integration, you will need administrator access to both your AWS environment and the Field Effect MDR Portal.
Setting Up the Integration
To enroll Amazon Web Services (AWS) for cloud monitoring, you’ll need to perform the following tasks:
Prepare AWS for the integration
Create a new AWS user.
Create the new user's Access Key.
Complete the Integration in the Field Effect MDR Portal
Prepare AWS for the Integration
The following sections outline the tasks you must complete in AWS before you configure the integration in the Field Effect MDR Portal.
Create a New AWS User
From the AWS Console, search for "IAM" in the search bar (Alt+S) and click the result. It will take you to the IAM Dashboard.
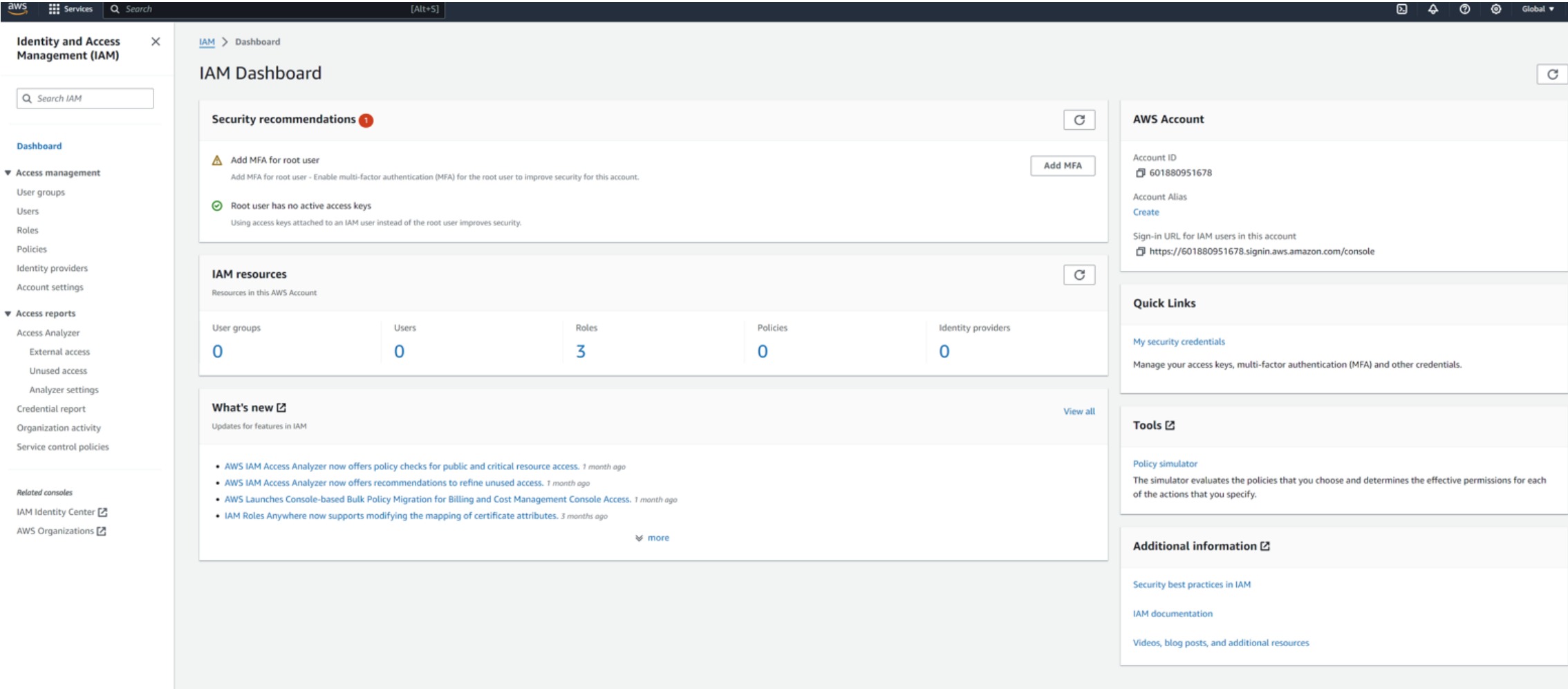
From the IAM sidebar options, select Users from the Access Management section.

From the Users page, click the Create User button

Give the user a relevant and memorable name ("Field Effect MDR User") and click Next.
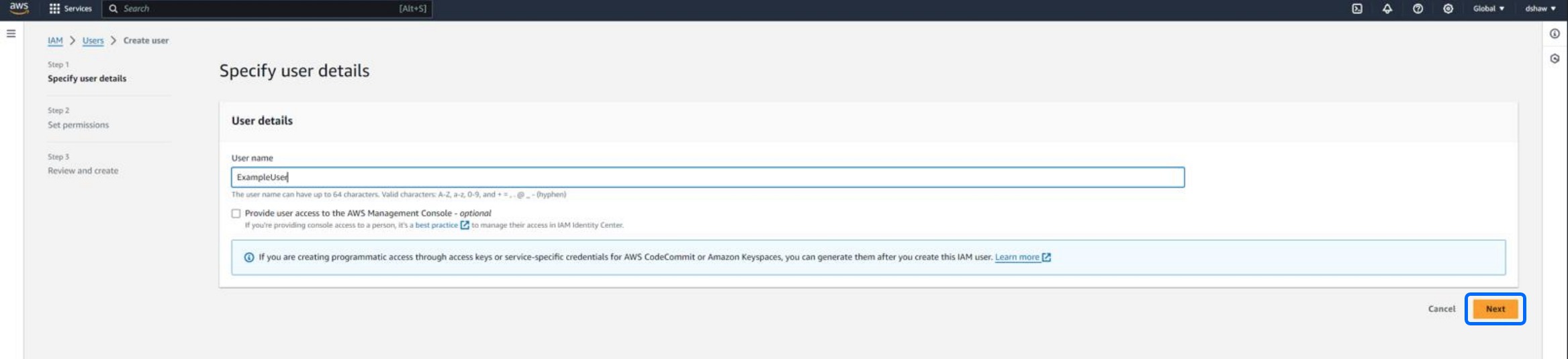
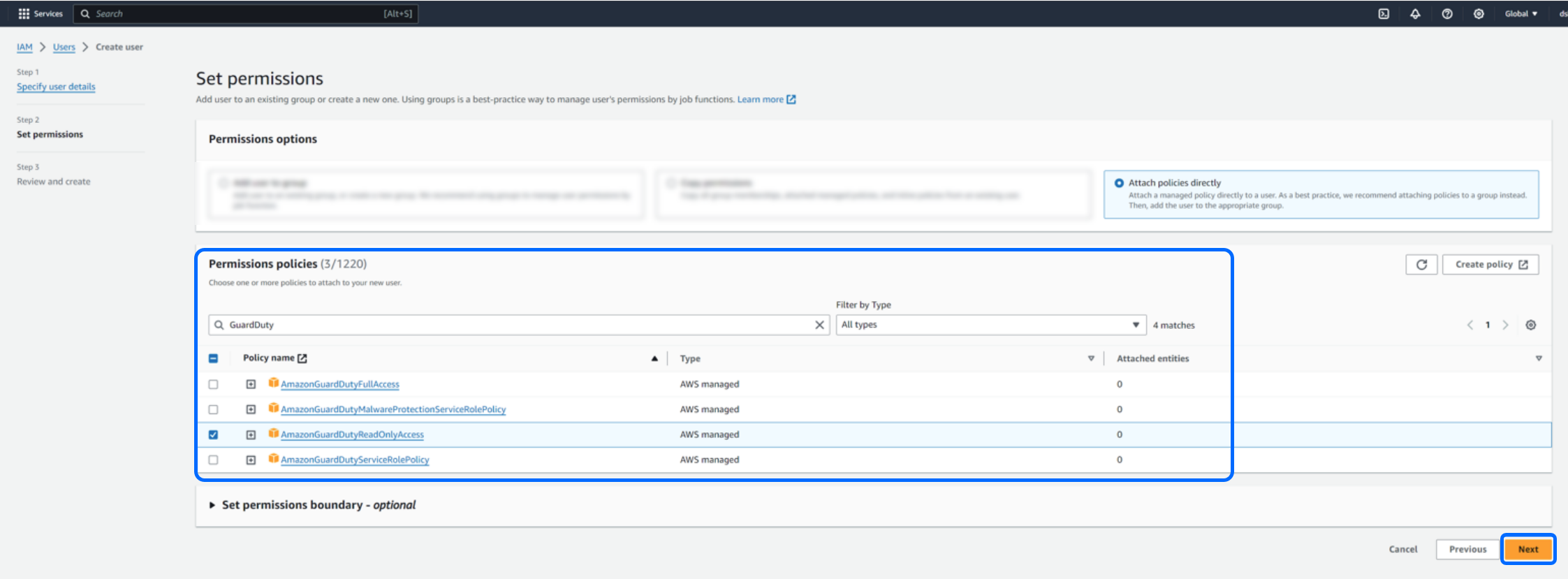
On the next step, you will need to set the permissions this user required for the integration. Set the user's permission option to Attach Policies Directly and add the following policies in the Permissions Policies section (use the search bar to find these polices):
AWSCloudTrailReadOnlyAccess
IAMReadOnlyAccess
AmazonGuardDutyReadOnlyAccess (optional)
After adding all four policies, click Next.
You'll be taken to the final confirmation page. When ready, click Create User. This will create the Field Effect MDR user for the integration.

Create the New User's Access Key
On the Users page, select the newly created user. Click on the username to drill into it.

In the Access Keys section, click Create access Key.
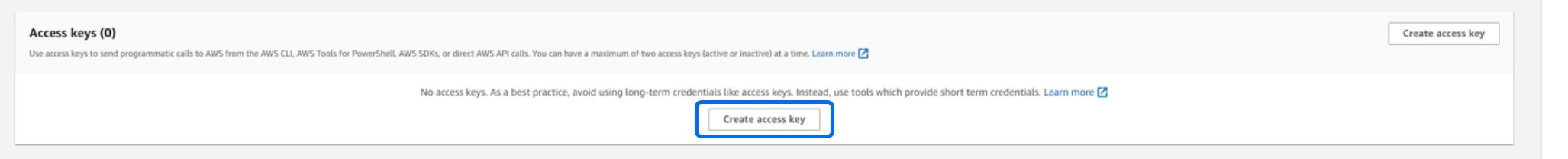
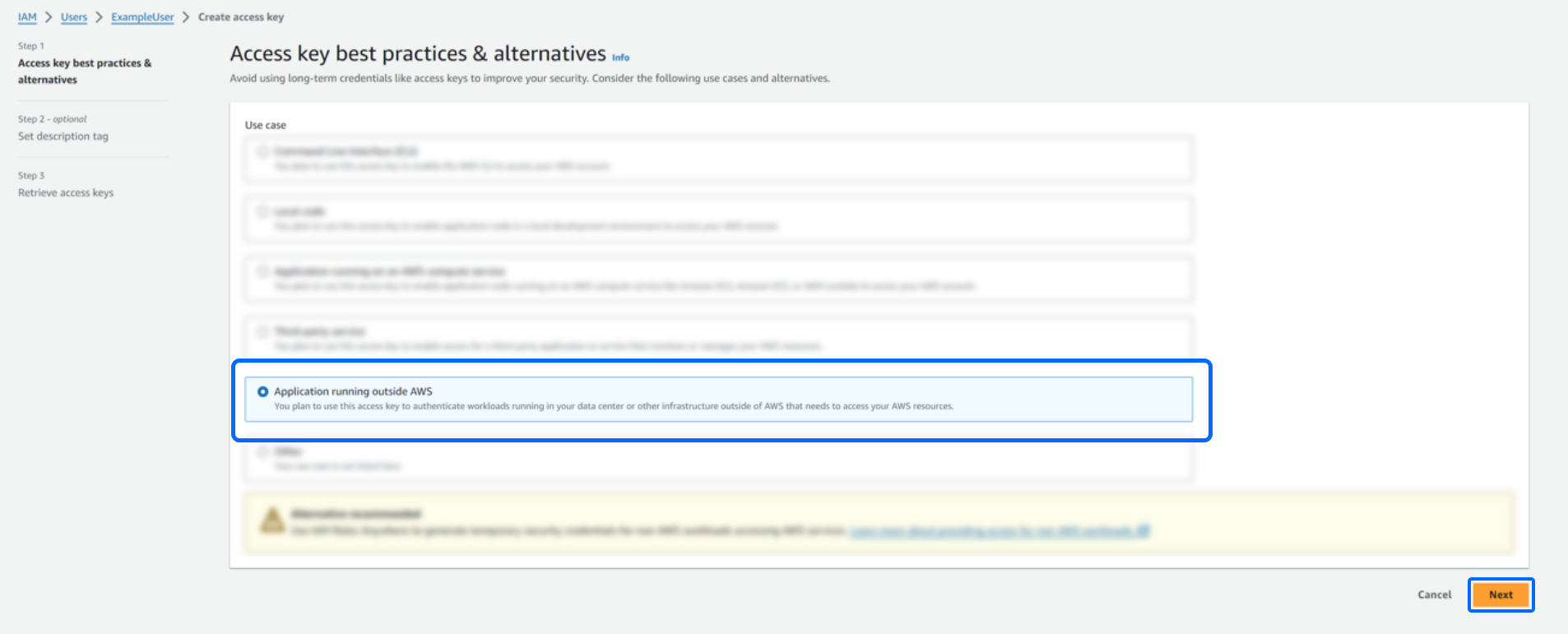
For step one, select Application Running Outside AWS for this key's use case. Click Next to continue.
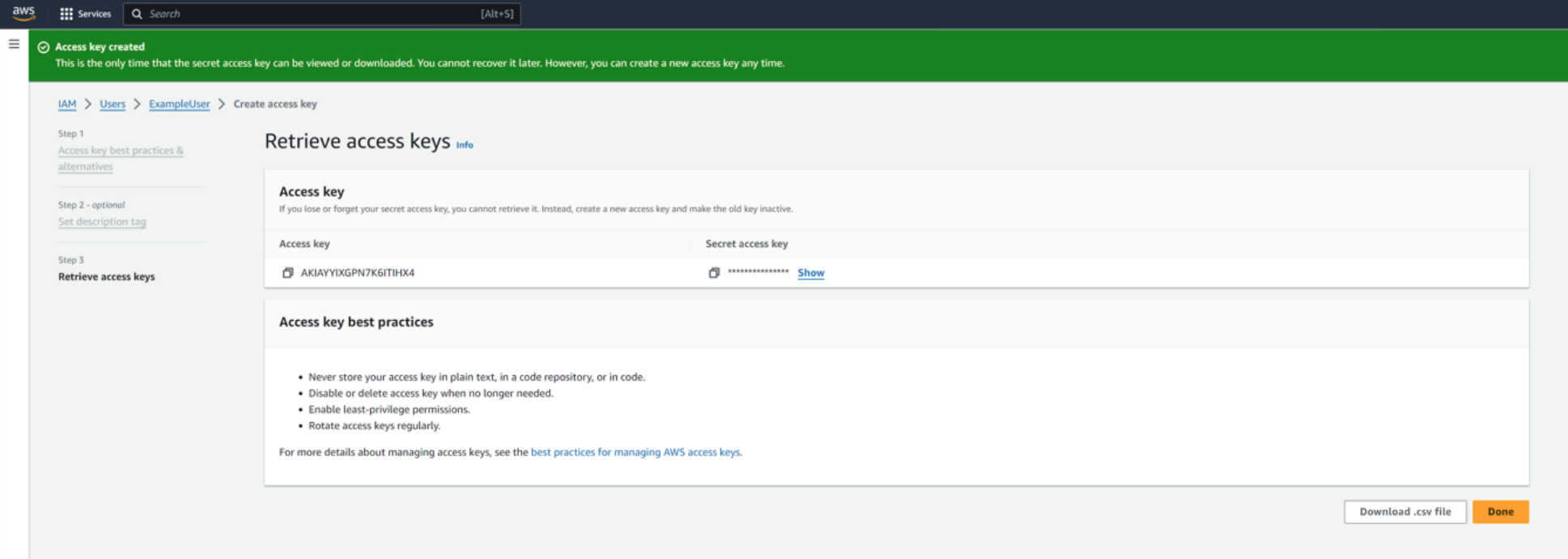
You'll be presented with the new Access Key, and an additional secret access key. Download the .csv file or copy both of these, as you will need them when completing the integration in the Field Effect MDR Portal.
Complete the Integration in the MDR Portal
Note for Partners: This procedure is performed on a per-client basis. Ensure that the Organization Selector is set to the appropriate client before continuing.
After you have prepared AWS for the integration (above), Navigate to the Field Effect Portal's Administration > Integrations page. From the Cloud monitoring tab, click Add.

The integration wizard will open. Paste the AWS Client ID and the AWS Client Secret you gathered in the previous procedure (Preparing AWS for the Integration) and click Add.

You'll be taken back to the integrations page, and the integration card will show that the integration is connected and promoted to the top, alongside any other connected integrations. Field Effect MDR will now have access to AWS's available reporting and generate AROs when appropriate.

Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article