Table of contents
- Table of contents
- Introduction
- Configure a Response Policy
- Enabling Active Response for a Cloud Service
- Disabling Active Response
- Active Response System Notifications
- Testing and Validating Notifications
- Troubleshooting
Introduction
For partners: this procedure is performed on a per-client basis. Ensure that the Organization Selector is set to the appropriate client before continuing.
When onboarding Field Effect MDR, an appliance (physical or virtual) was sent to you with our response policies preloaded, and the Balanced response policy enabled by default. When initially rolling out the service, our Balanced policy will only report on detected threats and not trigger any automated response action. This approach limits the chance of a response action impacting your operations while we understand your organization's network topology and expected behaviors. If a legitimate threat is discovered during this rollout, response actions will be triggered manually, once it has been reviewed by an analyst.
After we understand your organization, it’s endpoints, and their expected behavior, the Balanced response policy will start to actively respond to threats and vulnerabilities. This initial monitoring period typically takes place over a 10 to 20-day window, after the endpoint agent has been rolled out across all your devices. This monitoring period can be adjusted through a support request.
Enabling Active Response: FAQs
What if my organization has another EDR service or solution with blocking capabilities?
Exclusions to Active Protection can be made via the exclusions field in your organization’s Active Response Policy.
You will also receive an ARO notifying you if multiple EDR solutions are found. You can comment on this ARO to remediate the conflict.
During the rollout of Active Response, our analysts monitor each environment for any possible conflicts. We have also successfully co-existed with other EDR blocking features.
I am concerned that devices, resources, or networks may be negatively impacted by this. What safeguards are in place?
This feature is being rolled out to employ only “high confidence” blocking policies.
Will geo-location conditional access policies impact Active Response?
It may, and to ensure it doesn't create negative impacts, please allowlist the range 64.26.180.112/28, as this is the range that Active Response, and cloud monitoring, connect from.
Configure a Response Policy
This feature is enabled globally, so your selected response policy will be enabled across all endpoint devices with the agent installed. If you need to disable Active Response for a specific endpoint, or set of endpoints, this can be done using the bulk editing feature found on the MDR Portal's Devices page.
Visit our Help Center article to learn more about bulk editing endpoints.
By default, every organization is protected with the Balanced policy. There are four response policies available (Off, Limited, Balanced, Aggressive) for Active Response, and each policy supports custom exclusions and other requests (example: "never isolate this business-critical server").
The rest of this section steps through the process of configuring your response policy further.
Step 1 - Navigate to Active Response
From the Service Profile page, navigate to the Active Response card and click Response Policy. The current response policy will be shown in this section. In the example below, the Balanced policy (our default policy) is enabled.

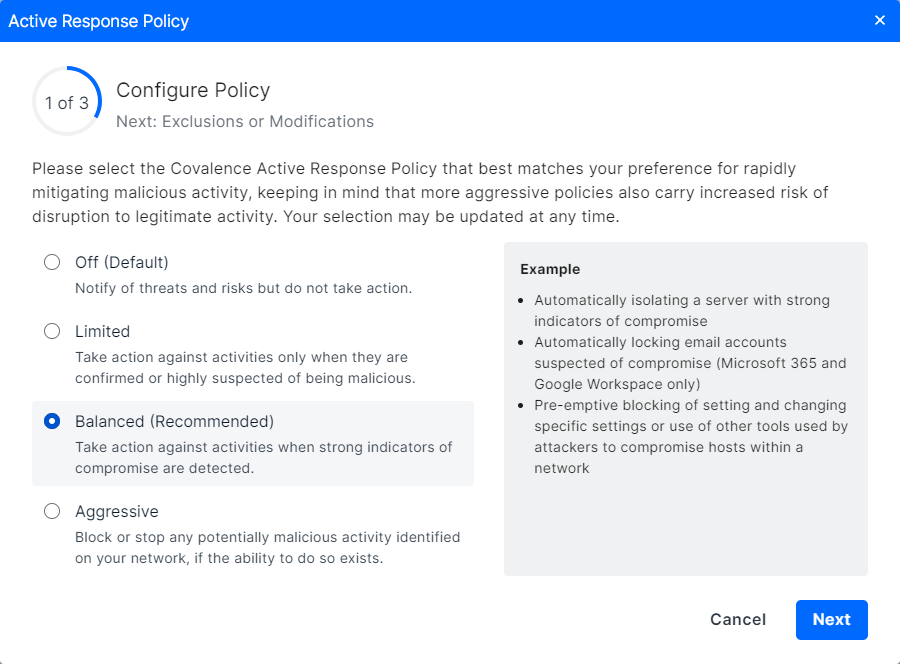
Step 2 - Set your policy
Selecting your preferred response policy and click Next.

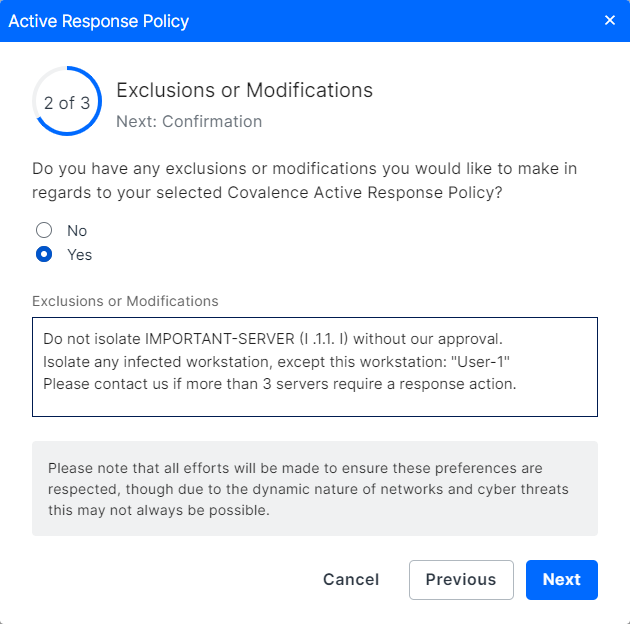
Step 3 - Add any Exclusions and Modifications
You can add custom exceptions and exclusions to the policy.
To do so, select the Yes checkbox and add your requests and comments in the Exclusions or Modifications field.
In the example below, the user has requested that a device with a specific IP address should be excluded, which will stop Active Response from triggering any response actions on that device.
When finished, click Next.
Step 4 - Review your profile
Review and confirm your policy settings.
When you're ready to publish the response policy, click Submit.
This will apply the changes you made to your response policy.

Step 5 - Done
You'll be taken back to the Service Profile page and your response policy will be listed. If you need to adjust your policy in the future, click on the policy to edit and make changes.

Enabling Active Response for a Cloud Service
Once a response policy is set, it can be enabled for supported cloud services, allowing Field Effect MDR to trigger response actions on cloud accounts suspected of being compromised.
Field Effect MDR blocks accounts using conditional access policies. So, if an M365 account is locked due to a security threat, the conditional access policy restricts access to any resources from that account, helping contain the compromise.
Active Response supports Microsoft 365 and Google Workspace, and the following prerequisites must be met:
- A response policy must be configured.
- Administrator credentials for the cloud service are required to enable active response for the cloud service.
- Your cloud subscription must support audit logging, and it must be enabled.
In the example below, Google Workspace has not been set up for cloud monitoring. In this case, click Add to enable cloud monitoring, and you will be prompted to enable Active Response during the process.
A new window will appear on your screen. To enable Active Response, select the Standard option and click Continue.
See our Integrations content for more on enabling Active Response for these services.
Note: this will not change an organization’s response policy. Selecting Standard from Limited will apply to the cloud service. If an aggressive policy is set, Standard will apply the aggressive policy to the cloud service. If an organization uses the Limited response policy, selecting Standard will apply the Limited.

Enabling Active Response for an Existing Integration
Partners: This feature must be enabled on a per-client basis. Ensure that the Organization Selector is set to the appropriate client before continuing.
Once the prerequisites are met (admin credentials available and audit logging enabled), navigate to the Integrations page (Administration Section) to enable Active Response for cloud services that have been enabled already, or when enabling a new integration.
In the example below, cloud monitoring has already been enabled for Microsoft 365, but Active Response was not enabled during the initial setup. Click the Active Response Policy Settings link to enable a response policy.

You'll be taken to the Service Profile's Active Response section. Once a policy is set, Active Response will become enabled for the cloud service.
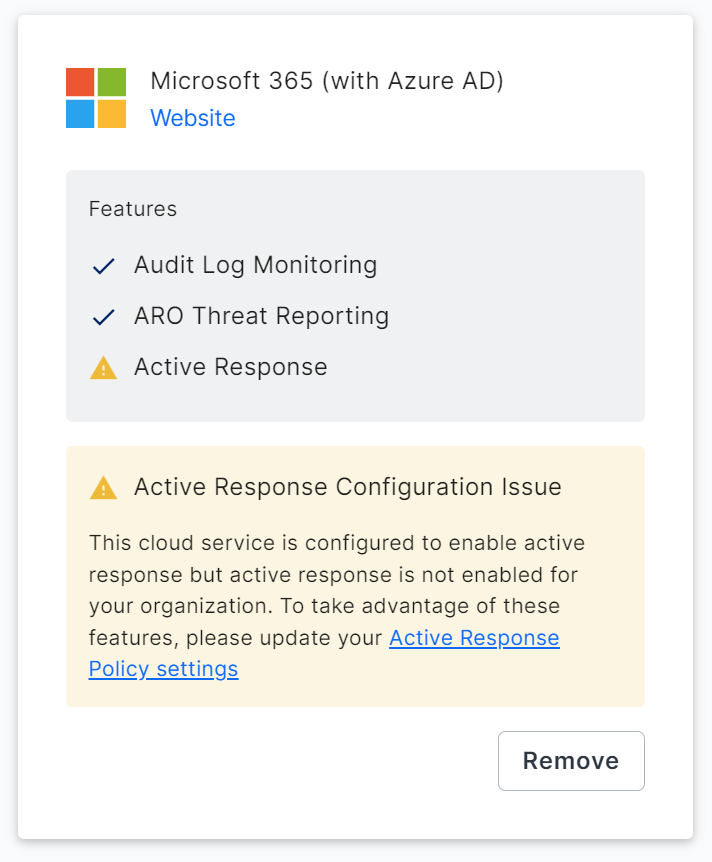
Troubleshooting Cloud Configurations
In the example below, Active Response has not yet been enabled for your organization. If you receive this error message, configure an Active Response policy before enabling Active Response for a cloud service.
Disabling Active Response
Disabling the feature globally
If you decide that you want to disable Active Response globally, then you can do so by opening the Response Policy section and selecting Off instead of the current response policy.
Disabling the feature for specific users
If you need to disable Active Response for a device(s) use the Devices page's Bulk Edit functionality.
With bulk editing, you can disable agent protection for only the devices that servicing, while keeping the rest of your fleet protected. See our Help Center article on Bulk Editing Endpoints.
Active Response System Notifications
Partners: notifications are enabled and customized on a per-client basis. Ensure that the Organization Selector is set to the appropriate client.
If Active Response triggers a response action on an endpoint device, a desktop notification will be generated for the end user. These notifications can be customized or disabled.
Notifications are available for the following scenarios:
- Field Effect detects a threat (ex: malicious software) on an endpoint device.
- Field Effect performs an action (ex: isolated from the network, rebooted, etc.) on an endpoint device.
- (Coming soon) A removable drive is detected and blocked on an endpoint device.
- (Coming soon) Disk scan results.
Notifications can be enabled, disabled, and customized from the Endpoint Agent page’s Agent Preferences section. Below is an example notification. This article walks through the process of customizing notifications.
Notifications support English, French, and Spanish, and the language is determined by the end user’s operating system settings. If the user has their operating system set to a supported language, the notification’s default message connect will be translated to their set language.
If you create a custom notification message, however, it will remain in the language it was written in.
Customizing Notification Messages
The System Notifications toggle must be enabled to customize System Notification messages.
Navigate to the Endpoint Agent page (Administration section) and click Customize System Notification Message.
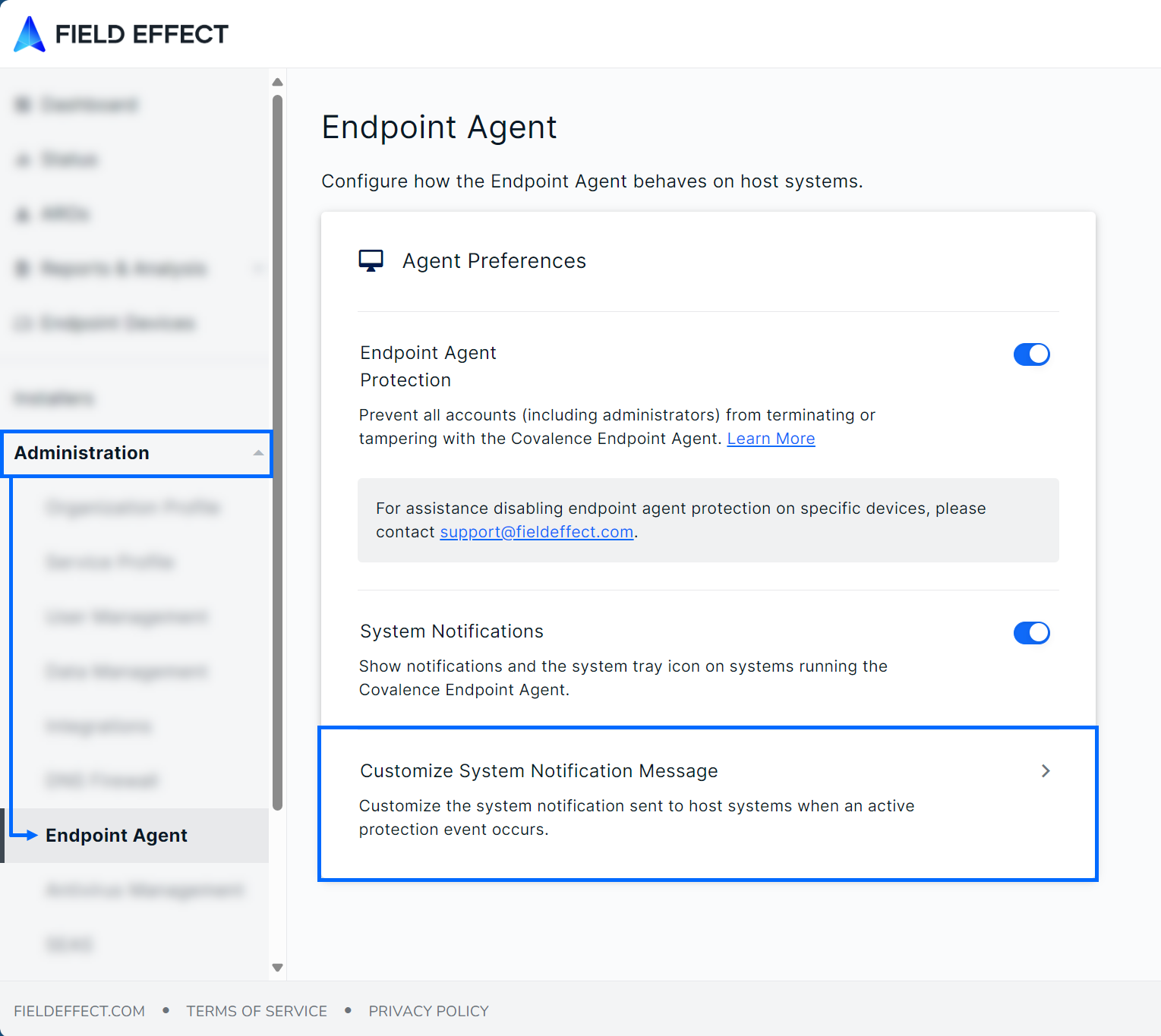
The Customize System Notification Message window will open. From here, you can choose to use the default messaging, custom messaging, or no messaging. The example below shows the messaging options available the messaging location in the notification is highlighted. If you select None, the highlighted area will be left blank. After making your selection, click Save.
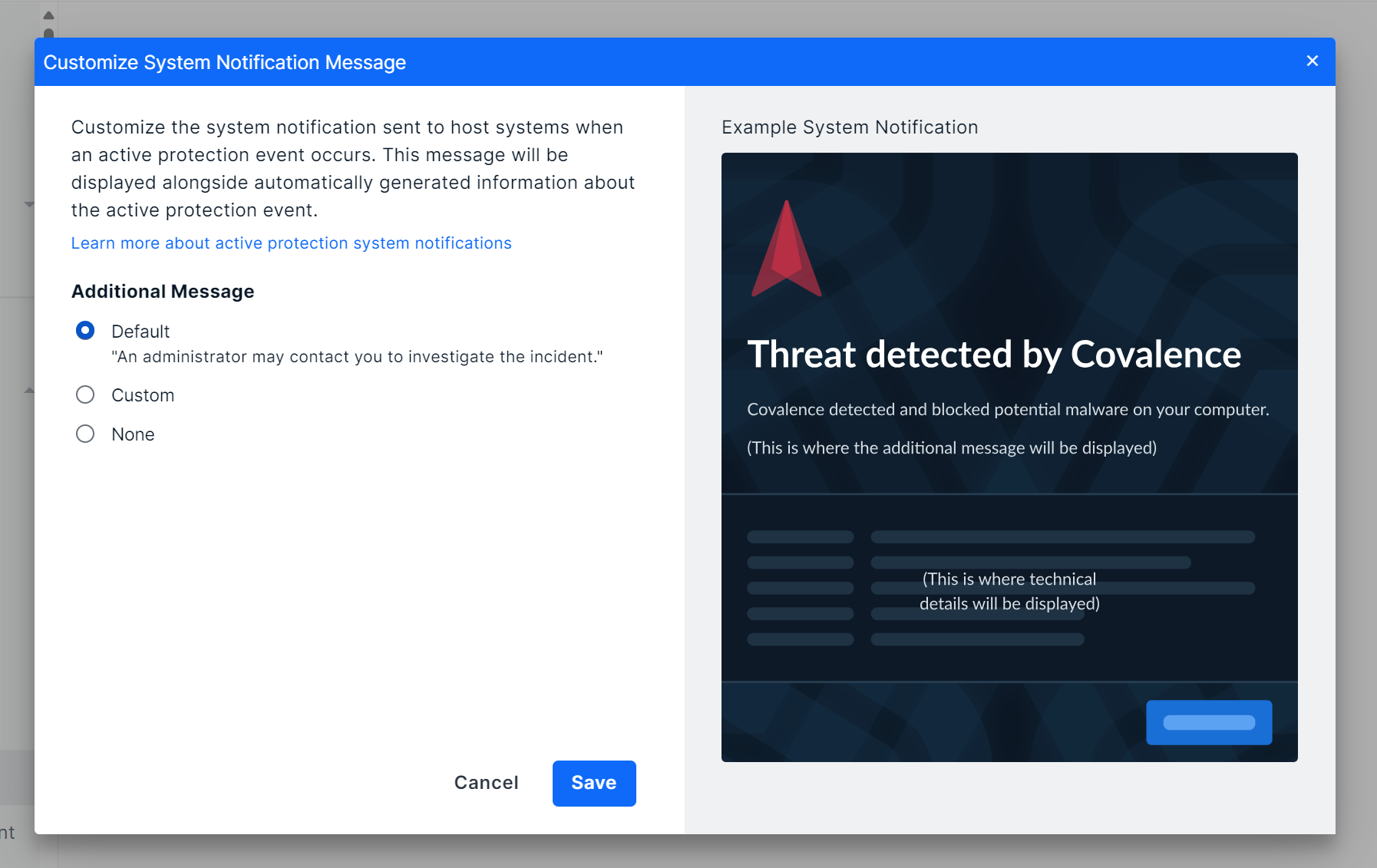
Using the Default Message
To use the default message (“an administrator may contact you to investigate the incident”), select Default and click Save. The default messaging will then be displayed in the notification.
Using No Messaging
If you want to remove the message entirely, select None and click Save. No messaging will be shown in the notification.
Using a Custom Message
If you want to create your own notification message, select Custom.
The Custom Message field will appear under the message options. Note that custom messaging has a 350-character limit, and some custom characters are unsupported (see Troubleshooting below).
Type your custom message into the field and click Save. Your message will be applied, and you will be taken back to the Endpoint Agent page.

Testing and Validating Notifications
If you want to receive a test notification to review and validate, Field Effect supports several workflows for sending test AROs and validating blocking capabilities.
To learn how to send a test notification, visit our Field Effect Endpoint Service Validation article and use the Notification Validation Test.
Troubleshooting
As mentioned previously, custom messaging has a 350-character limit. If you exceed this limit, you will not be able to save the message.
Also, some characters are not supported in the custom message. Using an unsupported character will produce an error (shown below) and you will not be able to save your message.
Supported special characters include:
- Alphabetical letters: a-z, A-Z
- Spanish letters and accents: Á, á, É, é, Í, í, Ó, ó, Ú, ú, Ñ, ñ
- French letters and accents: Ç, ç, É, é. Â, â, Ê, ê, Î, î, Ô, ô, Û, û, À, à, È, è, Ù, ù. Ë, ë, Ï, ï. Ü, ü
- Numerical characters: 0-9
- Special characters: “space”, “+”, “(“, “)”, “,” “,” “:” , “;” , “@”
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article